A brand-new side-channel attack affecting several generations of Intel CPUs has actually been found, permitting information to be dripped through the EFLAGS register.
The brand-new attack was found by scientists at Tsinghua University, the University of Maryland, and a computer system laboratory (BUPT) run by the Chinese Ministry of Education and is various than many other side-channel attacks.
Rather of counting on the cache system like lots of other side-channel attacks, this brand-new attack leverages a defect in short-term execution that makes it possible to draw out secret information from user memory area through timing analysis.
The attack works as a side channel to Disaster, an important security defect found in 2018, affecting lots of x86-based microprocessors
Disaster makes use of an efficiency optimization function called “speculative execution” to allow assailants to bypass memory seclusion systems to gain access to tricks saved in kernel memory like passwords, file encryption secrets, and other personal information.
Disaster has actually been mainly alleviated through software application spots, microcode updates, and hardware redesigns; nevertheless, no option has actually dealt with the issue 100%, and the most recent attack approach may work even in completely covered systems depending upon hardware, software application, and spot setups.
Short-term execution timing attack
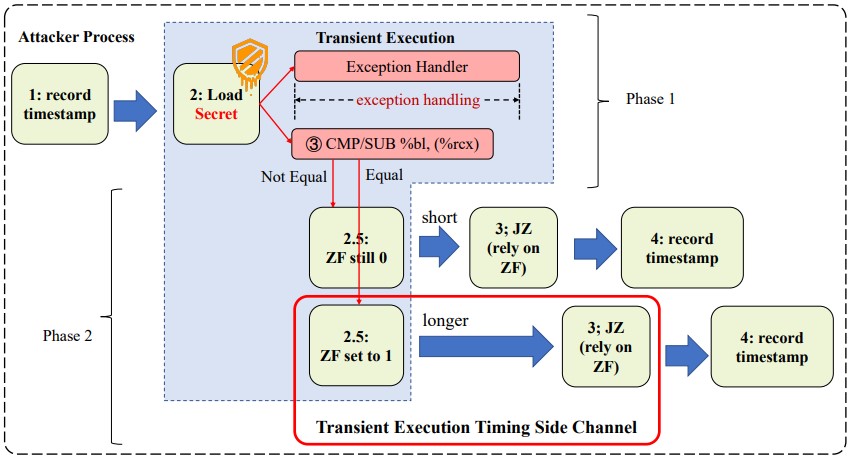
The brand-new side-channel attack provided in a technical paper released on Arxiv.org explains a defect in the modification of the EFLAGS register in short-term execution, impacting the timing of JCC (get on condition code) directions.
The EFLAGS register is a CPU register that holds numerous flags connected to the processor’s state, while the JCC guideline is a CPU guideline that permits conditional branching based upon the material of the EFLAGS register.
The attack is performed in 2 stages, the very first being to set off short-term execution and encode secret information through the EFLAGS register, and the 2nd is to determine the execution time of the KCC guideline to translate the information.
The speculative information revealed that the attack attained 100% information retrieval (leakage) for the Intel i7-6700 and Intel i7-7700 and had some success versus the more recent Intel i9-10980XE CPU. The experiment was carried out on Ubuntu 22.04 jammy with Linux kernel variation 5.15.0.
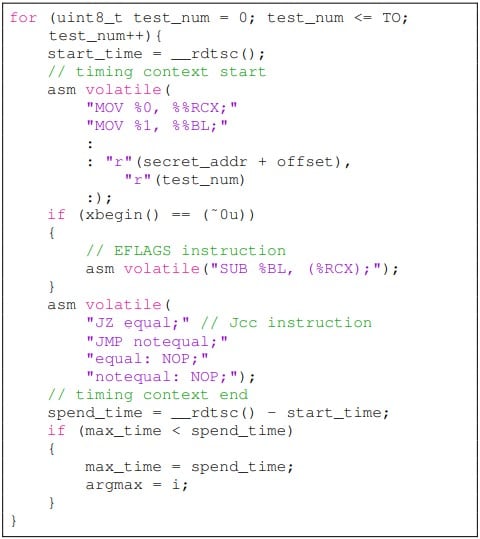
Nevertheless, the scientists keep in mind that this timing attack isn’t as dependable as cache-state side-channel approaches, and to improve lead to current chips, the attack would need to be duplicated countless times.
” In our experiment, we discovered that the impact of the EFLAGS register on the execution time of Jcc guideline is not as consistent as the cache state,” checks out the part about the examination of the speculative information.
” For about 6-9 cycles after the short-term carry out, the Jcc carry out time will not will build a side-channel. Empirically, the attack requires to duplicate countless times for greater precision.”
The scientists confess that the source of the attack stay evasive and assume that there’s a buffer in the execution system of the Intel CPU, which requires time to go back if the execution ought to be withdrawn, a procedure that triggers a stall if the taking place guideline depends upon the target of the buffer.
Nevertheless, they still propose some non-trivial mitigations, such as altering the execution of the JCC guideline to make adversarial execution determining difficult under any condition, or rewording the EFLAGS after short-term execution to minimize its impact over the JCC guideline.